Table of Contents
ToggleWhat are CYBER-ATTACKS?
A cyber attack is a set of actions performed by threat actors, who try to gain unauthorized access, steal data or cause damage to computers, computer networks, or other computing systems. A cyber attack can be launched from any location. The attack can be performed by an individual or a group using one or more tactics, techniques and procedures.
An overwhelming fact is that a cyber attack can cripple or even destroy a business of any size in a matter of seconds. The speed at which malicious actors can exploit vulnerabilities, access sensitive information, and disrupt operations underscores the critical importance of robust cybersecurity measures in today’s digital landscape. The potential consequences, from financial losses to reputational damage, highlight the need for businesses to prioritize and invest in comprehensive cybersecurity defenses.
The most heard names of cyber attacks are Malware, Phishing, Ransomware etc, which most of us are aware of. But here below, are some SCARIEST ATTACKS that can ruin businesses of any size, in SECONDS.
TOP 4 SCARIEST CYBER-ATTACKS-
FILE LESS MALWARE ATTACK! (EXTREMELY DANGEROUS!)
In regular malware attacks, there are files that antivirus programs can detect and remove. Fileless malware is different – it doesn’t use those typical malicious files. Instead of using harmful files, file-less malware will take advantage of tools and applications that are already there in your computer! These are tools your computer uses for regular, everyday tasks.
Because it can operate without being detected and use legitimate tools, fileless malware is especially dangerous. It can quietly do harmful things without you realizing it until the damage is done.
WATERING HOLE ATTACKS!
Imagine you have a favorite hangout spot, like a cafe or a park. In the digital world, websites can be like hangout spots for internet users.
Cyber attackers pay attention to the websites you frequently visit, just like someone might notice your favorite cafe.
Instead of targeting you directly, hackers go to the websites you love. They sneakily inject malicious code into these sites. When you visit the compromised website, the trap springs. The malicious code infects your device, MAKING THIS A VERY PERSONALIZED ATTACK!
JUICE JACKING!- Cyber Attack
Picture this: You’re in a crowded airport, and your phone battery is on its last breath. Desperate for a charge, you spot a public charging station. Little do you know, hidden in that harmless-looking USB port is a trap set by a cybercriminal.
As you plug in your phone, it’s not just getting a power boost – it’s also handing over sensitive information. The USB port, infected with malicious software, quietly snatches data from your device.
Evil Twin Wifi Attacks!
In an Evil Twin attack, hackers create a fake Wi-Fi hotspot that looks very similar to a legitimate one. It’s like they set up a trap by making a copycat version of the Wi-Fi connection you’d usually use. The tricky part is that the fake hotspot has a name that’s almost identical to the real one. Once connected, the hackers can intercept the data that users send and receive.
WHAT IS MFA? (Multi-Factor Authentication)
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource such as an application, online account, or a VPN.
Implementing multi-factor authentication (MFA) has now become standard practice for most organizations. Compared to using passwords alone, having MFA in place significantly strengthens account security by making it extremely difficult for hackers to bypass authentication – provided that it is properly configured and correctly used.
Hackers are getting clever in finding ways to get around the extra security step called secondary authentication. So, businesses shouldn’t think of this extra step (known as MFA) as unbeatable. They need to be watchful for any attempts by hackers to go around this additional security measure. Stay alert!
CAN HACKERS BYPASS MULTI-FACTOR AUTHENTICATION?
Yes ABSOLUTELY, hackers can bypass Multi-Factor Authentication (MFA) using various methods. MFA is an additional layer of security that requires users to provide two or more different factors of authentication to access an account or other internal system.

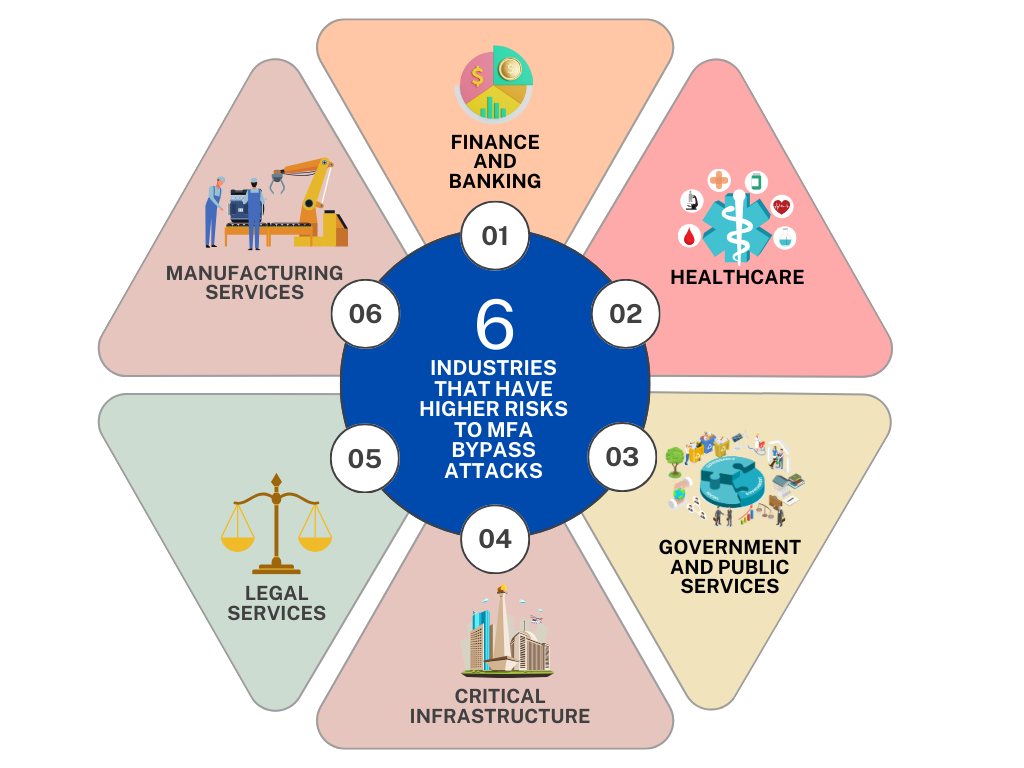
Certain industries may be more vulnerable to Multi-Factor Authentication (MFA) bypass attacks, and the level of vulnerability can vary based on the nature of the industry and its security practices.
Industries that handle sensitive information or are more frequently targeted by cybercriminals may face higher risks.
‘‘A STRONG DEFENSE IS THE BEST OFFENSE AGAINST CYBER THREATS’’
10 WAYS TO PREVENT MFA BYPASS ATTACKS.
Use Stronger Codes-
Instead of short, simple codes, go for longer and more complex combinations with letters and numbers. They’re tougher for hackers to crack.
Biometric Authentication Rocks-
Consider using biometrics like fingerprints as one of your security layers. It’s way harder for a hacker to replicate your thumbprint than guess a 4-digit code.
Smart Passwords Only-
Make sure your passwords are complex. Cybercriminals can easily figure out simple passwords, so go for a mix of letters, numbers, and symbols.
No Password Repeats-
Never reuse passwords- If a cybercriminal gets hold of one set of credentials, they shouldn’t be able to use them to break into other accounts.
Time-Based Passwords-
Use one-time time-based passwords (TOTP). This minimizes the window for hackers to crack the code, especially after a successful phishing attempt.
Skip SMS Authentication-
Avoid using SMS for authentication. SMS codes are easily compromised, so it’s better to choose more secure options.
Limit Unsuccessful Attempts-
Have a system in place that limits the number of failed MFA login tries. This stops hackers from making endless attempts to break in.
Train Your Team-
Educate your team regularly on cybersecurity, including MFA security. Teach them how to spot phishing emails and create strong passwords.
Watch Out for Unapproved Apps-
Be cautious about using apps that aren’t approved. Stick to known platforms to avoid falling into potential security traps.
Keep an Eye on Vulnerabilities-
Regularly check for weaknesses in your online assets. An attack surface management solution can help you spot and fix vulnerabilities before hackers exploit them.
Conclusion
TECHNOKRAFT GIVES YOU A FREE PEN TESTING AND A LOT MORE SURPRISES AND STRENGTH.
CHECK THE CURRENT REPORTS AND ANALYSIS OF YOUR THOROUGH CYBER ASSESSMENT
